Hide Yourself Online Using TOR Network
Nowadays, most internet users are fully aware of how they can be
tracked online easily. Irrespective of the fact that most online
platforms are well-intentioned and most honest, we ignore tiny piece of
information that sends out enormous details about our likes, our
dislikes, our means of transportation to our office including the
browser we desire most. Following some simple steps can reduce the rate
at which we get tracked, which includes switching off our location
server on our phones, frequently erasing our browser cookies and going
through the stress of logging out of our preferred social network sites
whenever we aren’t really using them. Sometimes however, we really want
to be unidentified, and stay invincible. Definitely, staying as
anonymous online is not only for crooks, activists and betrayers.
Tor is a well-developed and enhanced concealment tool which can be used to browse the regular World Wide Web or the alleged Dark Web.
On the common web, the websites locations are publicly displayed, but the user of Tor stays unidentified. With the Dark Web server, both the operator and the sites that they visit are unidentified and neither of them knows the real IP address of the other.
This is because, there are chains of computers between the hidden service and the user which is called “Tor circuit” or “Onion routing”, that randomly and intentionally bounces your web browsing traffic through a broadly circulated network of nodes handled by volunteers, thus in the Tor network, no personal connecting point will know where your traffic originated from and where it ended up.
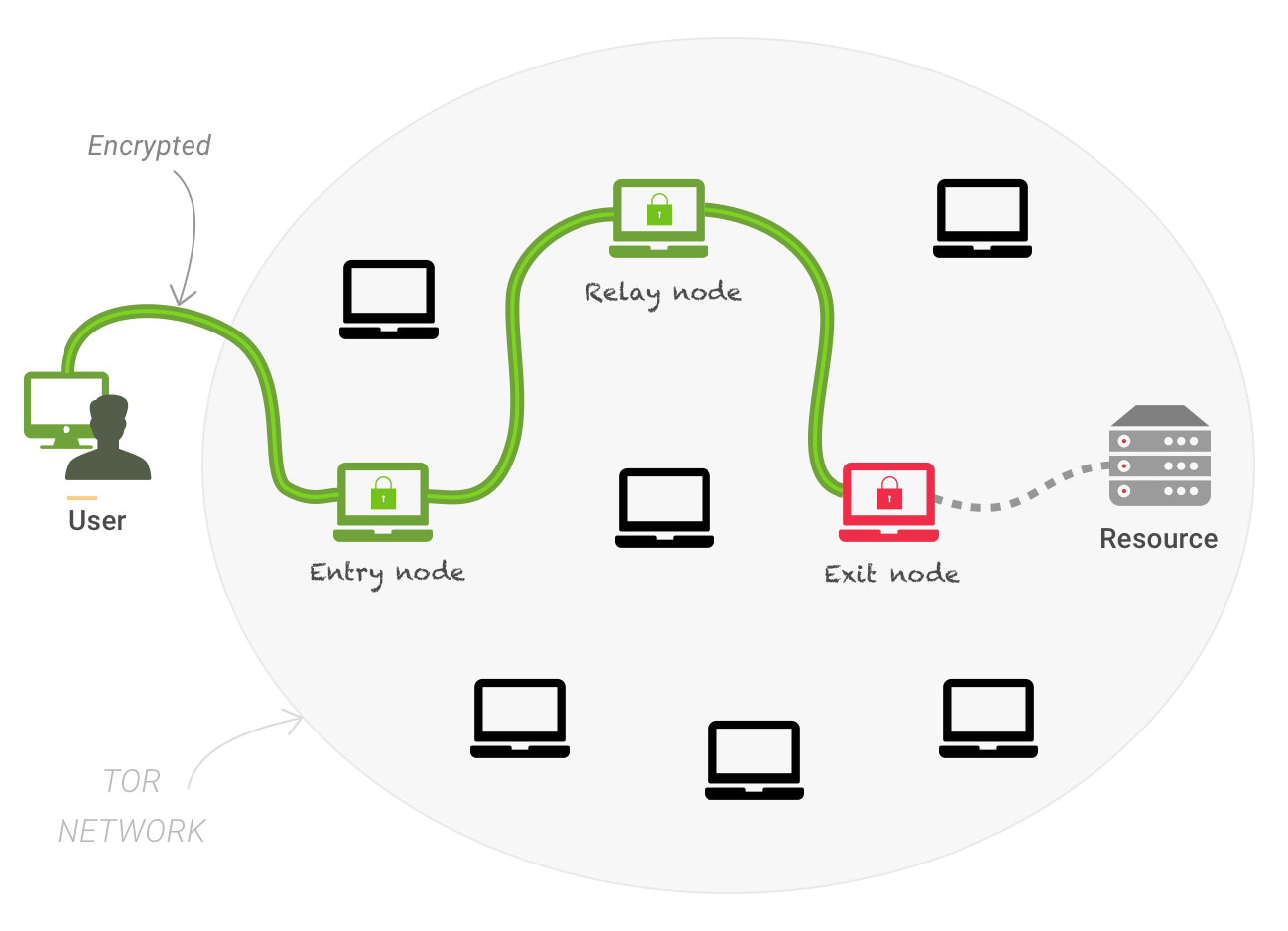
Most hackers and criminals love using Tor, certainly, because it assists them become invincible online, and it also assist them in keeping their servers running regardless of law enforcement agents who are looking for them in other to get them offline or seize their data.
Furthermore, if your traffic comes out of the onion network at the other end, the “Exit node” or “last Tor hop” knows exactly where you visited, even if you are still unidentified.
However that’s not all.
Tor is an onion router, and its duty is to direct the journey which your network traffic embarks on, whether you’re operating a browser that is generating requests, or you are using a server that’s creating replies.
Tor does not check what your network traffic contains.
If you let your name be known on a web form, or perhaps your server detects its location in one of its responses, Tor will not investigate deep into your traffic and resolve the criminal information.
Actually, for the reason that your traffic is within the onion network, the content of your packets cannot be seen by Tor, cheers to encryption that made it very difficult to comprehend how serious the users of your preferred dark web services are.
Having this in mind, We will see the summary of reports known as “Onion Scans” published by Privacy Researchers from Canada.
If you make use of Tor, though for completely definitive online activity, you should definitely see these reports.
In there are some fascinating surprises.
According to the recent report HTTPS is still very rare on the TOR network. Only a handful of sites have an active HTTPS endpoint, and only a tiny fraction of those present valid certificates.
Previous reports tells us that By getting connected to several Dark Web servers which are available and searching for similarities in the legal documents of the replies that came back, the investigators were able to find out which servers shared similar hosting company.
For example, once you connect to a remote server making use of a protocol known as “SSH protocol” (short for Secure Shell), you will receive a public encryption key by the server using it to keep your traffic private.
Preferably, when one server farm is generating SSH services for numerous users, it will make use of a special public/private key pair for each user, however that isn’t what always happens: one private key is frequently shared between all the SSH instances.
 So far the web server protects the one-size-fits all private key
safe, every other person is safe against hackers, so this convenience is
satisfactory.
So far the web server protects the one-size-fits all private key
safe, every other person is safe against hackers, so this convenience is
satisfactory.
However, it’s not considerably good within Tor, because the public key that is shared ties these users unnecessarily together in a bad way for privacy and secrecy.
(In the Onion Scan #3, almost a quarter of the SSH servers seen inside the Tor network shared a single SSH key, and were consequently hosted by a single user, a more substandard networking system than you might have imagined).
Likewise, the investigators observed that several FTP servers inside Tor had ignored some identifying information in their login banners; the “welcome note” that the server shows immediately you connect at first.
That’s similar with responding your telephone with somebody who has never called you before, by plainly and gradually saying your full names, rather than just saying Hello! And then you would be deliberating on how the caller knows who you are.
Tor is a well-developed and enhanced concealment tool which can be used to browse the regular World Wide Web or the alleged Dark Web.
On the common web, the websites locations are publicly displayed, but the user of Tor stays unidentified. With the Dark Web server, both the operator and the sites that they visit are unidentified and neither of them knows the real IP address of the other.
This is because, there are chains of computers between the hidden service and the user which is called “Tor circuit” or “Onion routing”, that randomly and intentionally bounces your web browsing traffic through a broadly circulated network of nodes handled by volunteers, thus in the Tor network, no personal connecting point will know where your traffic originated from and where it ended up.

Most hackers and criminals love using Tor, certainly, because it assists them become invincible online, and it also assist them in keeping their servers running regardless of law enforcement agents who are looking for them in other to get them offline or seize their data.
How Anonymous & Private is TOR?
The period your Tor traffic enters the Onion network, the connection point or node that appears first in the list which you will be connected with is called an “Entry guard”, this feature can indicate the particular area where you are connecting from; it is very difficult to avoid.Furthermore, if your traffic comes out of the onion network at the other end, the “Exit node” or “last Tor hop” knows exactly where you visited, even if you are still unidentified.
However that’s not all.
Tor is an onion router, and its duty is to direct the journey which your network traffic embarks on, whether you’re operating a browser that is generating requests, or you are using a server that’s creating replies.
Tor does not check what your network traffic contains.
If you let your name be known on a web form, or perhaps your server detects its location in one of its responses, Tor will not investigate deep into your traffic and resolve the criminal information.
Actually, for the reason that your traffic is within the onion network, the content of your packets cannot be seen by Tor, cheers to encryption that made it very difficult to comprehend how serious the users of your preferred dark web services are.
Having this in mind, We will see the summary of reports known as “Onion Scans” published by Privacy Researchers from Canada.
If you make use of Tor, though for completely definitive online activity, you should definitely see these reports.
In there are some fascinating surprises.
According to the recent report HTTPS is still very rare on the TOR network. Only a handful of sites have an active HTTPS endpoint, and only a tiny fraction of those present valid certificates.
Previous reports tells us that By getting connected to several Dark Web servers which are available and searching for similarities in the legal documents of the replies that came back, the investigators were able to find out which servers shared similar hosting company.
For example, once you connect to a remote server making use of a protocol known as “SSH protocol” (short for Secure Shell), you will receive a public encryption key by the server using it to keep your traffic private.
Preferably, when one server farm is generating SSH services for numerous users, it will make use of a special public/private key pair for each user, however that isn’t what always happens: one private key is frequently shared between all the SSH instances.

However, it’s not considerably good within Tor, because the public key that is shared ties these users unnecessarily together in a bad way for privacy and secrecy.
(In the Onion Scan #3, almost a quarter of the SSH servers seen inside the Tor network shared a single SSH key, and were consequently hosted by a single user, a more substandard networking system than you might have imagined).
Likewise, the investigators observed that several FTP servers inside Tor had ignored some identifying information in their login banners; the “welcome note” that the server shows immediately you connect at first.
That’s similar with responding your telephone with somebody who has never called you before, by plainly and gradually saying your full names, rather than just saying Hello! And then you would be deliberating on how the caller knows who you are.
Any Queries? Feel free to comment below..
The best way to THANK US is by clicking the share button below.
Join our WhatsApp Broadcasting channel-
Add 8359925962 to your contacts.
Send a message MAXD-TRICKS TO 8359925962

Comments
Post a Comment